As many of us knows that latest version of Windows 10 won’t backup registry hives which could be needed when Windows 10 won’t boot because of registry errors. The HKEY_USERS contains data required each loaded user profile, and will be used by Winlogin to implement any specific user changes. This section will also contain keys relating to user security identifiers for that profile. This will generate an event log entry whenever the value of the registry or its subkeys are queried. Lastly, we want to make sure that the Principal is set to Everyone so that all users are audited.
- There’s nothing quite like realizing your Windows PC, Mac, or laptop is infected with a virus or malware.
- Others can be added by installing extras later on.
- The safest way to fix DLL file missing or corrupted errors thrown up by your Windows operating system would be to run the built-in System File Checker, which will replace missing or corrupted system files.
In the pop-up window, click Restart on the bottom right corner. Then you can see a list of functions keys, just press the F4 key on your keyboard to enable Safe Mode. If there is a list of restore points , select the Restore point that you want to recover and click Next. Is a Windows diagnostic troubleshooting tool that can help you repair Windows operating system when failing to log into the computer. This method often can be used to fix the problem with some corrupted or missing system files. You can follow my day-to-day project updates on social media. Be sure to follow me on Twitter at @DavidGewirtz, on Facebook at Facebook.com/DavidGewirtz, on Instagram at Instagram.com/DavidGewirtz, and on YouTube at YouTube.com/DavidGewirtzTV.
The odds are that the particular file is a target for the software to get in or that it is a commonly infect area. As with a PC, it is a good idea to equip your Mac with strong protection. AVG AntiVirus for Mac is a free and comprehensive cybersecurity tool that detects and blocks malware, spyware, ransomware and other security risks in real time. And it’s updated automatically to safeguard your Mac against the latest online threats. It’s a good idea to use a reliable security software to help remove macro viruses.
Core Aspects In Dll Files Examined
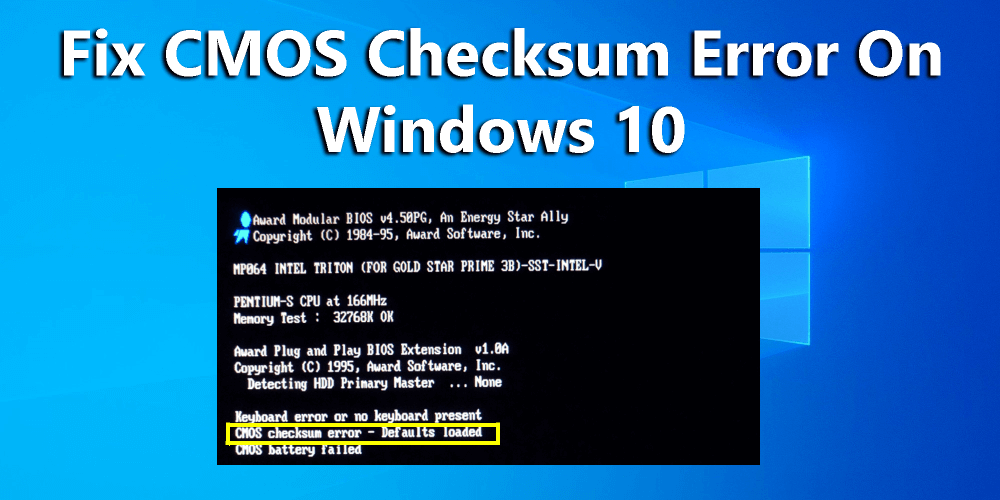
Then, the Configuration Manager searches the list of free cells for the hive in which the new key will reside to determine whether cells exist that are large enough to hold the new key cell. If not, the Configuration Manager allocates a new bin and uses it for the cell, placing any space at the end of the bin on the free cell list. The new key cell fills with pertinent information—including the key’s name—and the Configuration Manager adds the key cell to the subkey list of the parent key’s subkey-list cell. Finally, the system stores the cell index of the parent cell in the new subkey’s key cell. By using bins, instead of cells, to track active parts of the Registry, NT minimizes some management chores. For example, the system usually allocates and deallocates bins less frequently than it does cells, which lets the Configuration Manager manage memory more efficiently.
Root Criteria Of Dll – Insights
You can do so with the Group Policy Editor and Windows Registry, but you might not want to take action yet. Windows 10 version 21H2 corefoundation.dll missing is also in the works, and you will block it as well if you disable feature updates. I took the ISO route two days ago since my defer period was close to ending. Nothing disappeared, nothing new was installed and it seems everything runs faster.
